- Ethical Hacking Statement
- The Modern Security Operations Center
- The Windows Operating System
- Linux Basics
- Network Protocols
- Ethernet and IP Protocol
- Connectivity Verification
- Address Resolution Protocol
- The Transport Layer
- Network Services
- Network Communication Devices
- Network Security Infrastructure
- Attackers and Their Tools
- Common Threats and Attacks
- Network Monitoring and Tools
- Attacking the Foundation
- Attacking What We Do
- Understanding Defense
- Access Control
- Threat Intelligence
- Public Key Cryptography
- EndPoint Protection
- Endpoint Vulnerability
- Technologies and Protocols
- Network Security Data
- Evaluating Alerts
- Working with Network Security Data
- Digital Forensics and Incidents Analysis and response
1. A host is transmitting a broadcast. Which host or hosts will receive it?
- A. the closest neighbor on the same network
- B. all hosts in the same network
- C. all hosts on the Internet
- D. a specially defined group of hosts
A broadcast is delivered to every host that has an IP address within the same network.
2. Which statement describes a characteristic of cloud computing?
- A. Applications can be accessed over the Internet by individual users or businesses using any device, anywhere in the world.
- B. Devices can connect to the Internet through existing electrical wiring.
- C. Investment in new infrastructure is required in order to access the cloud.
- D. A business can connect directly to the Internet without the use of an ISP.
Cloud computing allows users to access applications, back up and store files, and perform tasks without needing additional software or servers. Cloud users access resources through subscription-based or pay-per-use services, in real time, using nothing more than a web browser.
3. A network administrator can successfully ping the server at www.cisco.com, but cannot ping the company web server located at an ISP in another city. Which tool or command would help identify the specific router where the packet was lost or delayed?
- A. netstat
- B. telnet
- C. ipconfig
- D. traceroute
The traceroute command provides connectivity information about the path a packet takes to reach the destination and about every router (hop) along the way. It also indicates how long a packet takes to get from the source to each hop and back.
4. Which OSI model layer contains protocols for process-to-process communication?
- A. Application Layer
- B. Transport Layer
- C. Session Layer
- D. Network layer
The application layer of the OSI model is responsible for communication between processes. Examples of protocols at the application layer are DHCP, DNS, and HTTP.
5. At which OSI layer is a destination port number added to a PDU during the encapsulation process?
- A. Application Layer
- B. Transport Layer
- C. Session Layer
- D. Network layer
6. What process involves placing one PDU inside of another PDU?
- A. Flow Control
- B. Encapsulation
- C. Encoding
- D. Segmentation
When a message is placed inside of another message, this is known as encapsulation. On networks, encapsulation takes place when one protocol data unit is carried inside of the data field of the next lower protocol data unit.
7. A web client is receiving a response for a web page from a web server. From the perspective of the client, what is the correct order of the protocol stack that is used to decode the received transmission?
- A. Ethernet, IP, TCP, HTTP
- B. HTTP, TCP, IP, Ethernet
- C. Ethernet, TCP, IP, HTTP
- D. HTTP, Ethernet, IP, TCP
1. HTTP governs the way that a web server and client interact.
2. TCP manages individual conversations between web servers and clients.
3. IP is responsible for delivery across the best path to the destination.
4. Ethernet takes the packet from IP and formats it for transmission.
8. In computer communication, what is the purpose of message encoding?
- A. to convert information to the appropriate form for transmission
- B. to interpret information
- C. to break large messages into smaller frames
- D. to negotiate correct timing for successful communication
Before a message is sent across a network it must first be encoded. Encoding is the process of converting the data message into another format suitable for transmission across the physical medium. Each bit of the message is encoded into a pattern of sounds, light waves, or electrical impulses depending on the network media over which the bits are transmitted. The destination host receives and decodes the signals in order to interpret the message.
9. How does BYOD change the way in which businesses implement networks?
- A. BYOD requires organizations to purchase laptops rather than desktops
- B. BYOD users are responsible for their own network security, thus reducing the need for organizational security policies
- C. BYOD devices are more expensive than devices that are purchased by an organization
- D. BYOD provides flexibility in where and how users can access network resources
A BYOD environment requires an organization to accommodate a variety of devices and access methods. Personal devices, which are not under company control, may be involved, so security is critical. Onsite hardware costs will be reduced, allowing a business to focus on delivering collaboration tools and other software to BYOD users.
10. Which two Internet connection options do not require that physical cables be run to the building? (Choose two.)
- A. DSL
- B. Celular
- C. Satellite
- D. dialup
- E. dedicated leased line
11. Which interface allows remote management of a Layer 2 switch?
- A. the AUX interface
- B. the console port interface
- C. the switch virtual interface
- D. the first Ethernet port interface
In a Layer 2 switch, there is a switch virtual interface (SVI) that provides a means for remotely managing the device.
12. A technician configures a switch with these commands: What is the technician configuring?
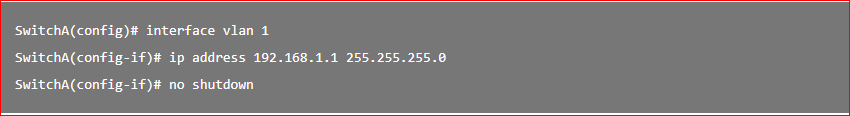
- A. Telnet access
- B. SVI
- C. password encryption
- D. physical switchport access
For a switch to have an IP address, a switch virtual interface must be configured. This allows the switch to be managed remotely over the network.
